Using Azure Key Vault to Store Client Secret for Graph API in Power Automate
3 min read

If you are using Graph API in your Flows, you may want to safeguard client secret as it will be shown in plain text when you store the client secret value in a variable, its value will show up in the Flow history. This blog assumes that you have already created Graph API, app registration in your Azure AD and you want to use Graph API in your Flow. Please note you need a license to use Premium Connectors for Power Automate.
Let’s get started by creating Azure Key Vault if one is not created in your Azure environment
1. Create new Azure Key Vault
-
- Go to Azure Portal -> Key Vault
- On Create Key Vault Screen, select Subscription, resource group and provide Key Vault Name and click on “Next: Access policy >” button
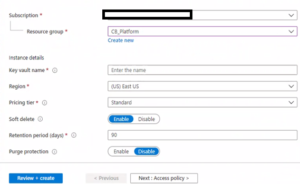
- Leave the default settings for access policy and click on the “Next: Networking” button
- Leave the default settings for access policy and click on “Next: Tags” button
- Leave the default settings for access policy and click on “Next: Review + Create” button
- Review the details and click on “Create” Button
Now let’s create the Secret in Azure Key Vault, to store the client’s secret value.
2.Create Secret
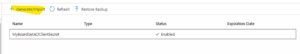
- Go to your newly created Key Vault and click on “Secrets” on the left nav
- Click on Generate/Import button
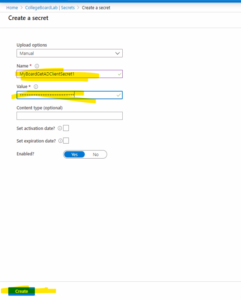
- Provide the name of the Secret “MyBoardGetADClientSecret” and provide the value of the Secret and click on Create button.
- Once Secret is created, we will now modify the Power Automate Flow to use Azure Key Vault in order to fetch the client secret value to be used in Graph API Http call
Create/Modify the Flow
-
- Edit your Flow or create new Flow
- Add new “Get Secret” action to the flow (before the HTTP action, if your Flow already exists and uses HTTP action for graph API)
![]()
-
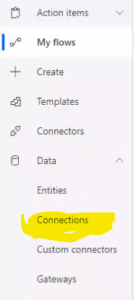
- At this point the “Get Secret” action might show an error, that is okay. If your Get Secret action shows an error, then without saving the flow navigate to Data – > Connections. If you don’t see an error then jump to step 7.
-
- On Connections Page, you will see the “Azure Key Vault” connection and in the status column, you will see “Parameter value missing”.
![]()
-
- Select the “Azure Key Vault” connection and click on the edit button.
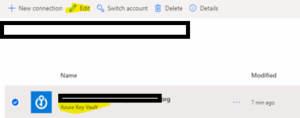
-
- Provide your Azure Key Vault name and click on the Save button.
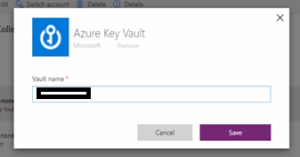
-
- Now go back to the Flow, and add the “Get Secret” action, just verify the connection of the “Get Secret” Action, it should not show any error in connection.
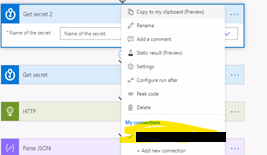
-
- Select the name of Secret in the “get secret” action
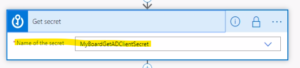
-
- Click on “Settings” of Get Secret action
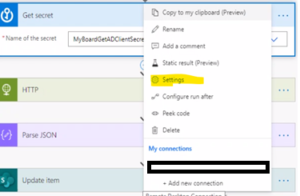
-
- Turn on the “Secret Inputs” and “Secret Outputs” settings and click on the “Done” button.
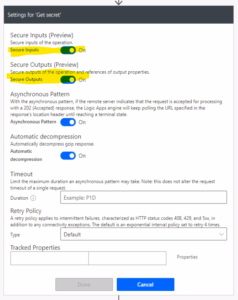
-
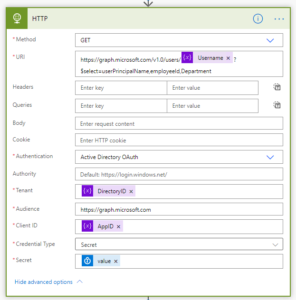
- Now in HTTP action, configure the parameter as follows:
- Method: GET (as I was using the Get – Graph API method)
- URI: Your graph API URL – here I am using Graph API to get user information
- Authentication: Select “Active Directory OAuth”
- Tenant: Store Directory ID value in a variable and use the variable in Tenant value. The Directory ID/Tenant ID you can find from Azure Portal
- Audience: https://graph.microsoft.com
- Client ID: the client id value when you created the App Registration for your Graph API
- Secret: use the dynamic value “Value of Secret” as shown in below screenshot
- Now in HTTP action, configure the parameter as follows:
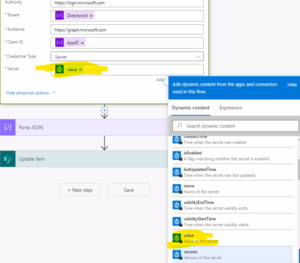
- Save the Flow and now the Flow should be able to communicate with Azure Key Vault to get the secret value.
- Then you can use Parse JSON action in order to read values returned by Graph API HTTP call.

